 Respect For Students!
Respect For Students!School officials have abused our children's most basic human rights by stealing and sharing their personal information. But they don't want to talk about that. Nor do they want to adopt strong policies that will protect our children. Instead, they try to distract us by talking about technology. But when the smoke clears, the technology is really quite simple. We must take physical control of our children's data by moving it back to our own district premises from its current location in Minnesota. Only at home is it clear that local school officials are not the owners but merely "caretakers" of the data. Only at home can we credibly assure that our data is available only to local school staff and student families.
| Data with Strangers (Current, Bad) | Data at Home (Past and Future, Good) | |
|---|---|---|
|
|
|
Why did our school officials steal our students' data away to Minnesota? Is it really about technology? Or is it more about their attempt to assert ownership over our children's personal information?
Among the official excuses have been some real whoppers:
Some school board members say they aren't certain whether or not it is "technically feasible" to store our children's data in the district. Have they truly forgotten that all student data was stored on computers here in the district for many years before they recently decided to take it away from us and hand it over to strangers?
To refresh their fading memories, some U-32 board members asked that the school technology director report on the feasibility of hosting our student data here at home. Unsurprisingly, he reported that hosting our student data at home is indeed feasible. Although he did not address the significant security risks that arise from our current outsourcing, he basically told the truth.
When they didn't get the message they wanted, the board attempted to rewrite the director's testimony in their meeting minutes. Decide for yourself! Compare the unedited video of the October 2, 2013, meeting (click on "School Board Meetings") to the board's official minutes. The differences are telling.
Until recently, the school has always internally hosted student data servers, and has never ceased internal operation of its print and email servers. The claim that locally hosting our own student data is technically problematic is just another excuse from school officials who want to assert their control over that data.
One excuse for snatching away our students' personal data is the false claim that it is safer in Minnesota than here at home. The most basic security analysis strongly suggests that our data is at least as safe --- and probably safer --- here than in Minnesota.
Security professionals analyze the security of information systems by identifying assets, threats, and vulnerabilities. Then, some level of risk is ascribed to each possible attack. Finally, possible countermeasures are evaluated against that risk. Each table below presents a partial security analysis for storing our student records. The first table analyzes security for keeping our student data at home; the second table analyzes security when an outside vendor controls our student data. Comparing the two tables helps clarify why our children's data is safer at home.
| Security Analysis: Local Storage and Control of Student Information | ||||||
|---|---|---|---|---|---|---|
| Item | Asset | Threat | Vulnerability | Likelihood | Potential Damage | Countermeasures |
| 1 | Student Data | Disclosure | Physical Attack on Hosting Site | Very Low | Very High | Door locks/alarm, Volume encryption |
| 2 | Student Data | Corruption | Physical Attack on Hosting Site | Very Low | Low | Door locks/alarm, Regular backups |
| 3 | Student Data | Loss | Physical Attack on Hosting Site | Very Low | Low | Door locks/alarm, Regular backups |
| 4 | Student Data | Disclosure | Local Attack on Host Computer | Low | Very High | Least privilege, Separation of duty |
| 5 | Student Data | Corruption | Local Attack on Host Computer | Low | Low | Least privilege, Separation of duty, Regular backups |
| 6 | Student Data | Loss | Local Attack on Host Computer | Low | Low | Least privilege, Separation of duty, Regular backups |
| 7 | Student Data | Disclosure | Network Attack on Host Computer | Medium | Very High | Verifiably secure host software |
| 8 | Student Data | Corruption | Network Attack on Host Computer | Medium | Low | Verifiably secure host software, Regular backups |
| 9 | Student Data | Loss | Network Attack on Host Computer | Low | Low | Verifiably secure host software, Regular backups |
Established security doctrine defines risk as the probability of a successful attack multiplied by the potential cost of that attack. Here, this definition is applied using qualitative, ordinal-level measures (e.g., "low," "medium," "high"), because precise numerical assessments are not necessary for this high-level, comparative study.
| Security Analysis: Outsider Storage and Control of Student Information | ||||||
|---|---|---|---|---|---|---|
| Item | Asset | Threat | Vulnerability | Likelihood | Potential Damage | Countermeasures |
| 1 | Student Data | Disclosure | Physical Attack on Hosting Site | Very Low | Very High | Security guards, Volume encryption |
| 2 | Student Data | Corruption | Physical Attack on Hosting Site | Very Low | Low | Security guards, Regular backups |
| 3 | Student Data | Loss | Physical Attack on Hosting Site | Very Low | Low | Security guards, Regular backups |
| 4 | Student Data | Disclosure | Local Attack on Host Computer | Medium | Very High | Least privilege, Separation of duty |
| 5 | Student Data | Corruption | Local Attack on Host Computer | Low | Low | Least privilege, Separation of duty, Regular backups |
| 6 | Student Data | Loss | Local Attack on Host Computer | Low | Low | Least privilege, Separation of duty, Regular backups |
| 7 | Student Data | Disclosure | Network Attack on Host Computer | High | Very High | Verifiably secure host software |
| 8 | Student Data | Corruption | Network Attack on Host Computer | Medium | Low | Verifiably secure host software, Regular backups |
| 9 | Student Data | Loss | Network Attack on Host Computer | Low | Low | Verifiably secure host software, Regular backups |
The tables address three threats to student data.
Insofar as data disclosure is clearly the gravest threat, differences between the two tables in rows 4 and 7 highlight one of the biggest security impacts of surrendering our children's data: the most common disclosure attacks are less likely when our data is here at home.
Comparing the two tables at row 4 suggests that, with respect to local attacks, our data is safer at home. Local attacks on the host computer are those involving direct physical access to the server system or its console. Accordingly, operational staff probably enjoy the greatest opportunity for such attacks, and they often also enjoy elevated system access privileges. An attack might involve direct copying of student data from the server onto a USB flash drive or other storage device. Alternatively, an attack might involve installation of altered software or configuration files that would allow subsequent unauthorized access over the network. The more numerous staff in a large vendor installation entails a higher aggregate probability that at least one will defect or err. In addition to the obvious individual incentives of bribes by criminal or government operatives, when personal information is consigned to for-profit enterprises (e.g., AT&T), sometimes even corporate management may be complicit, thereby reducing deterrent among employees. In contrast, local school administrators are untroubled by profit motive, and the less numerous local IT staff frequently have children enrolled in the school district or are personally acqainted with those whose personal information is at risk; vendor staff lack these community attachments.
Comparing the two tables at row 7 suggests that, with respect to network attacks, our data is safer at home. By using software that is similar or even identical to that used by the vendor, our student records will be equally well protected from remote network attacks. However, records stored in Minnesota are probably much more at risk, because they are pooled with 6.5 million others and pose a much more attractive target for cyber-criminals or government spies.
Network attacks are countered mainly by secure system and application software. The analysis presented here assumes that identical or nearly identical software protects student data whether it resides here in the district or in Minnesota. Protection against network attack is strongest when the deployed software is "verifiably secure" --- that is, the source code for the software is open to inspection, study, and improvement by the public. Over time, data security and system reliability will improve as verifiably secure systems based on free, open-source software are deployed by schools to address their IT needs. Schools that internally own and control their IT infrastructure will benefit sooner from this evolution, because they will not be constrained by proprietary vendor business models.
Physical attacks on a hosting site might include vandalism, burglary, or natural disaster. In order to counter direct physical attacks on the hosting site, our school technology director advised installing some additional door locks. Physical attacks on IT infrastructure are relatively unlikely, and attacks that result in information disclosure are even more unlikely. However, if warranted by the level of risk, a conventional alarm system, possibly with remote monitoring, could be an inexpensive additional countermeasure. Although larger facilities sometimes employ security guards, their value in countering the most threatening disclosure attacks on student data may be less than merely encrypting the data when offline.
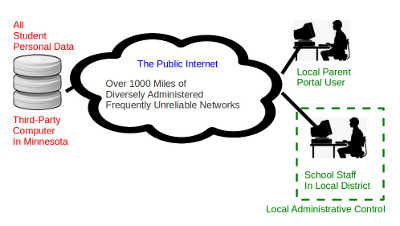
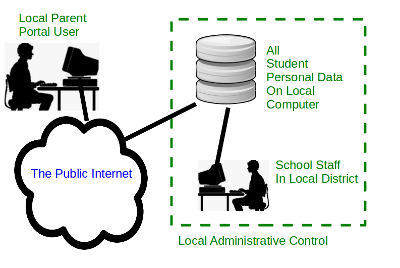
It's just common sense that keeping our student data here in the local school district will provide faster, more reliable access than keeping it in Minnesota. It's not that the vendor doesn't try: they guarantee that their server computers will be up and running 99% of the time. That's an average of only 15 minutes of downtime each and every day. But it's hard for Vermonters to know whether or not that guarantee is being fulfilled, because, try as they might, the vendor cannot control the performance or availability of the public Internet. The figure entitled Data With Strangers, shows how, when the data is not kept at home, access to student data by everyone, including our teaching staff, must traverse the public Internet. That's at least 1000 miles of interconnected transmission links and network devices, owned and operated by any number of independent communication providers. Congestion or device failure at any point along the way can noticably degrade performance or even make the server unavailable. Because Internet routing is both dynamic and collaborative, any given transaction might pass through Washington, DC, San Francisco, or Boston. In contrast, the Figure entitled Data At Home shows how, when student data is kept at home, all users are closer to it. School staff will likely notice the greatest improvement, and parent access should improve as well --- unless perhaps you live in Minnesota.
The reliability and security of student records is significantly improved by regular backups of the digital data. Our local IT staff already responsibly performs such backups. Moreover, our local school district is richly blessed by seven, independent, geographically distinct locations (our schools and district office) at which (encrypted) data backups could be stored. With these advantages, do our student records also need to be stored in Minnesota?
We need strong local policies that keep our data at home because only the people of this community truly care about our children's basic rights and privacy. We need to keep our children's data at home because only our local school staff can be held even remotely accountable for keeping it safe. In the unlikely event that there is a security breach related to student data stored here at home, you will probably hear about it. Do you think you will hear about any breaches all the way from Minnesota? Whatever else it accomplished, stealing the data away to Minnesota has certainly eliminated any accountability for our local staff.
Nobody in Minnesota is likely to be held accountable either. If you discover that your personal information has been disclosed, could you sue the vendor? In Minnesota court? Without legal standing? Without a compelling demonstration of tangible harm? Consult your attorney, but it doesn't sound especially promising.
Alternatively, you could file a complaint against our local school officials with the U.S. Department of Education. Yes, that's the same US DOE whose regulatory re-interpretation of the FERPA law permits school officials to seize and transfer ownership of student data in the first place.
If the school chooses to continue with the software currently in use, then the vendor will impose an additional annual payment of $6000-7000 for bringing the data home -- ostensibly for providing computer hardware on which their software would execute locally. Perhaps the most troubling aspect of this otherwise modest expense is the possibility of viewing it as a ransom for returning our children's data home. Choosing to use a particular software package should not bind our community to any vendor's political agenda. We shouldn't have to surrender our children's personal information in order to get good administrative software at a good price.
Local operation of a student information server is not rocket science and imposes few if any incremental costs. Wild claims to the contrary are belied by the facts and are not consistent with reasonable technical consensus. The school district currently employs at least 6 full-time, qualified technical professionals, in addition to at least 5 technical professionals who are focused directly on the needs of the elementary schools. This staff currently operates email servers and print servers on which the operation of our schools depends daily. Until September 2012, this same staff for many years operated a student information server used to store and manage our students' personal information. Stealing that information and transferring it to Minnesota did not result in any significant staff or budget reductions. The incremental cost of bringing our children's data home -- even if we continue with the same software vendor -- is negligible.
The strongest and cheapest strategy for securing our students' rights is to deploy a student information system based on transparent, easily modified, open-source software running on school-owned, locally-resident commodity computer hardware. Such a strategy requires more careful thought and planning but frees us from any vendor's agenda.
Local storage of student records will not prevent parent access to their child's information via a parent portal. Existing Internet capacity at the schools is almost certainly sufficient to accommodate an internally hosted portal server. If needed, the federal E-Rate program allows link capacity to be added at very low cost. After all, a "portal" is just a website, not some high-tech miracle.
School officials have sometimes given the false impression that providing a parent portal requires their stealing student information and sharing it with their confederates. By cloaking their agenda in technical myth, they exploit parents' natural interest in their children to popularize their misdeeds. Moreover, this narrowness of purpose also excludes from consideration easier, cheaper alternatives for communication (e.g., secure email, commercial hosting, social media) that are enabled by a more transparent agenda.
Detailed Analysis
According to the WCSU Tech Plan (2012-2015, page 16), each school in our district currently enjoys at least 2.5Mb/s outbound bandwidth. Assume (lavishly) that each parent portal interaction consumes approximately 1Mbit. Assume 900 high school parents and that, in order to optimize TCP protocol performance, average link utilization should target 50 percent or less. Then, link capacity would be unacceptably over-subscribed only in the unlikely event that all parents simultaneously sought portal access within a single 12 minute period. Similar calculations apply to each elementary school, except that the number of parents is dramaticaly less.
By these calculations, each local school can probably host its own parent portal using only existing link capacity. Indeed, the five elementary schools might be able to share a single portal server without increasing local link capacity. However, if all district schools shared a single server, then either peak performance expectations would have to be relaxed (e.g., 1700 parents over 23 minutes), or more Internet capacity (perhaps one or two T-1 equivalents) would be required. Each additional T-1 link costs approximately $400/mo, before applying the Federal E-rate discount of 50 to 80 percent. Thus, each school's decision to share a portal server turns in part upon whether the savings on one-time computer purchase warrants the ongoing expense of any required link capacity.
Under any of the scenarios sketched above, the throughput of a portal server is unlikely to be limited by the processing overhead of SSL transactions. Rather, much of the perceived performance burden of an SSL transaction arises from network latency, because its initial handshake entails multiple round trips. For example, informal measurements show that, using 4096-bit cryptographic keys, an Intel Pentium Dual T3200 processor running at 2GHz can perform 11.8 RSA signatures per second. See also Goldberg, et al., A Comparison of HTTP and HTTPS Performance (Slides).
Chuck has been deeply involved in Internet technology and policy throughout his professional life. He worked on the first commercial internet router and developed the first business web hosting service. He co-authored the technology specifications used to manage the Internet and supervised overall development of management standards in the official Internet standards body. He served as chief technology officer for a global Internet access and hosting provider, supporting 100,000 business customers in 28 countries. He holds multiple graduate degrees and is currently completing a dissertation on user freedom in computer networks. He is the proud parent of two U-32 students.